Kubernetes-APIServer
[TOC]
深入理解Kube-APIServer
大纲
认证
鉴权
准入
- Mutating(变形)
- Validating (校验)
- Admission
限流
APIServer对象的实现
Shell
解码base64,转换为jwt |
API Server

访问控制预览
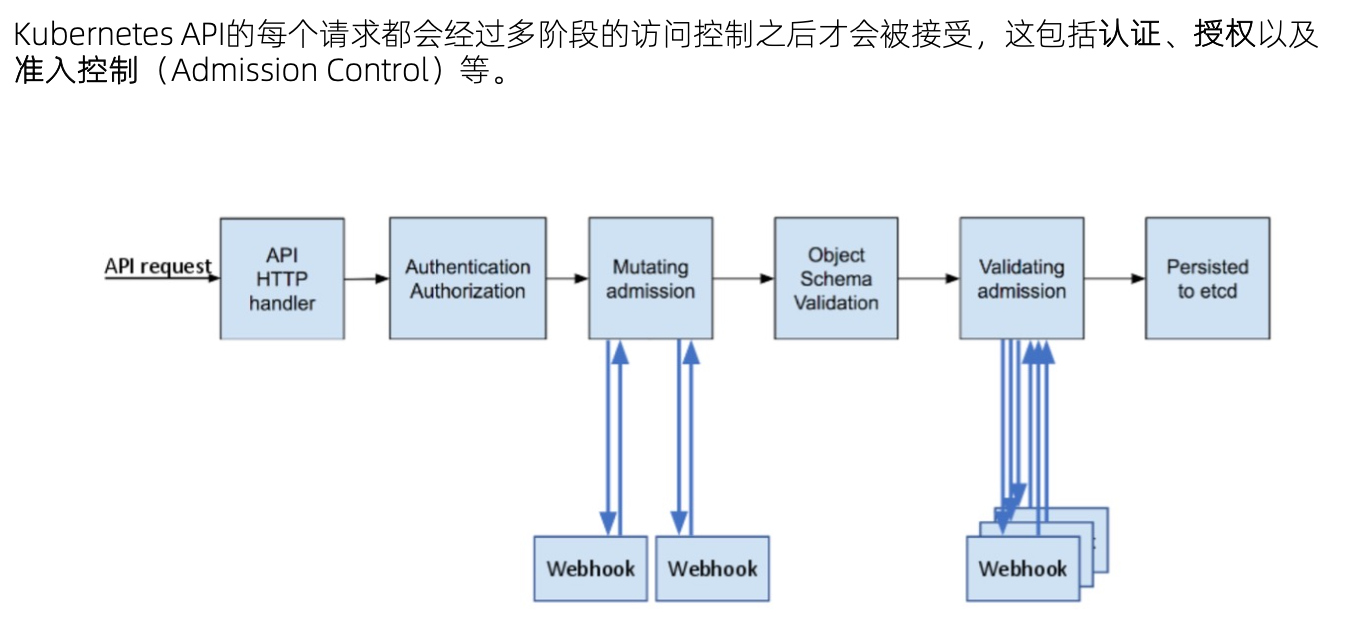
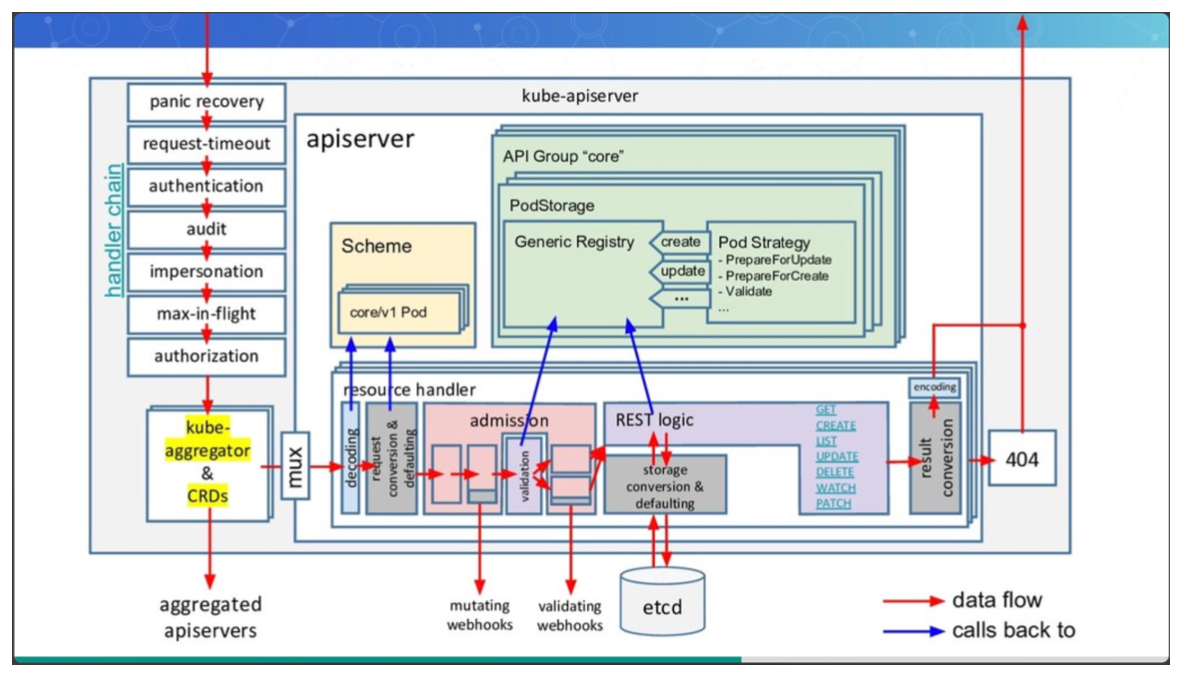
访问控制细节
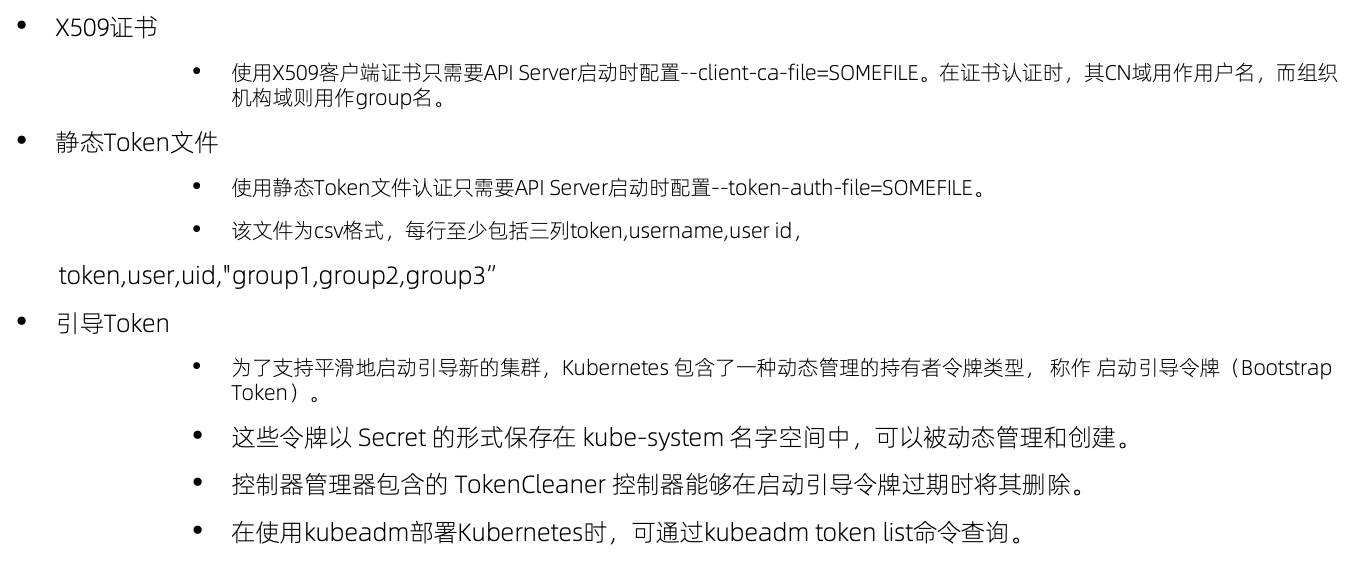
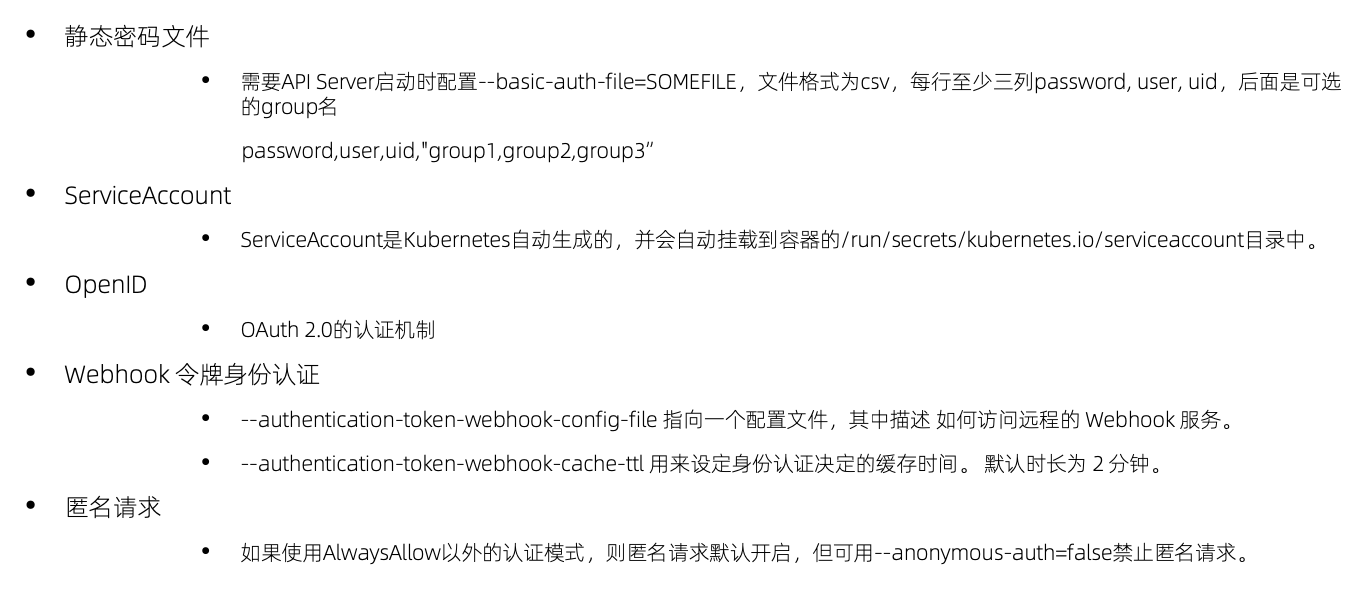
认证

认证插件
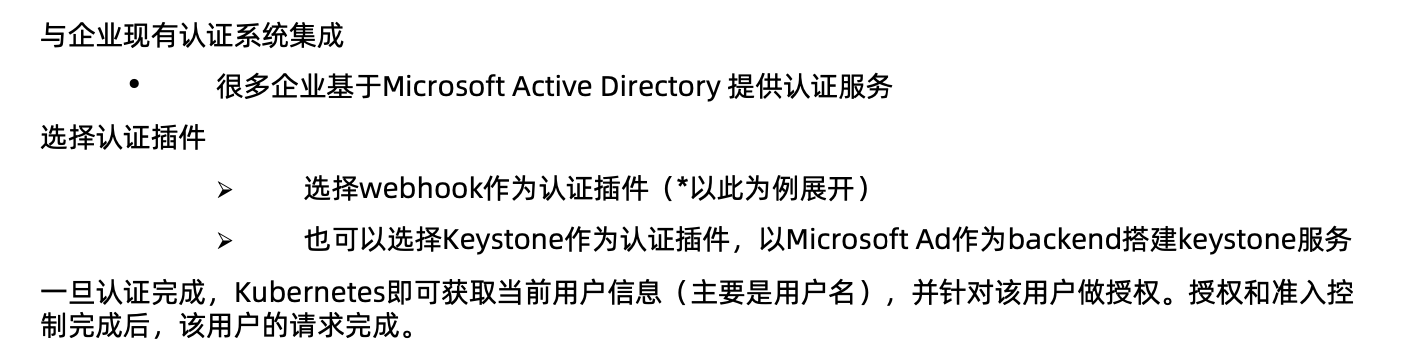
基于webhook的认证服务集成
构建符合kubernetes规范的认证服务
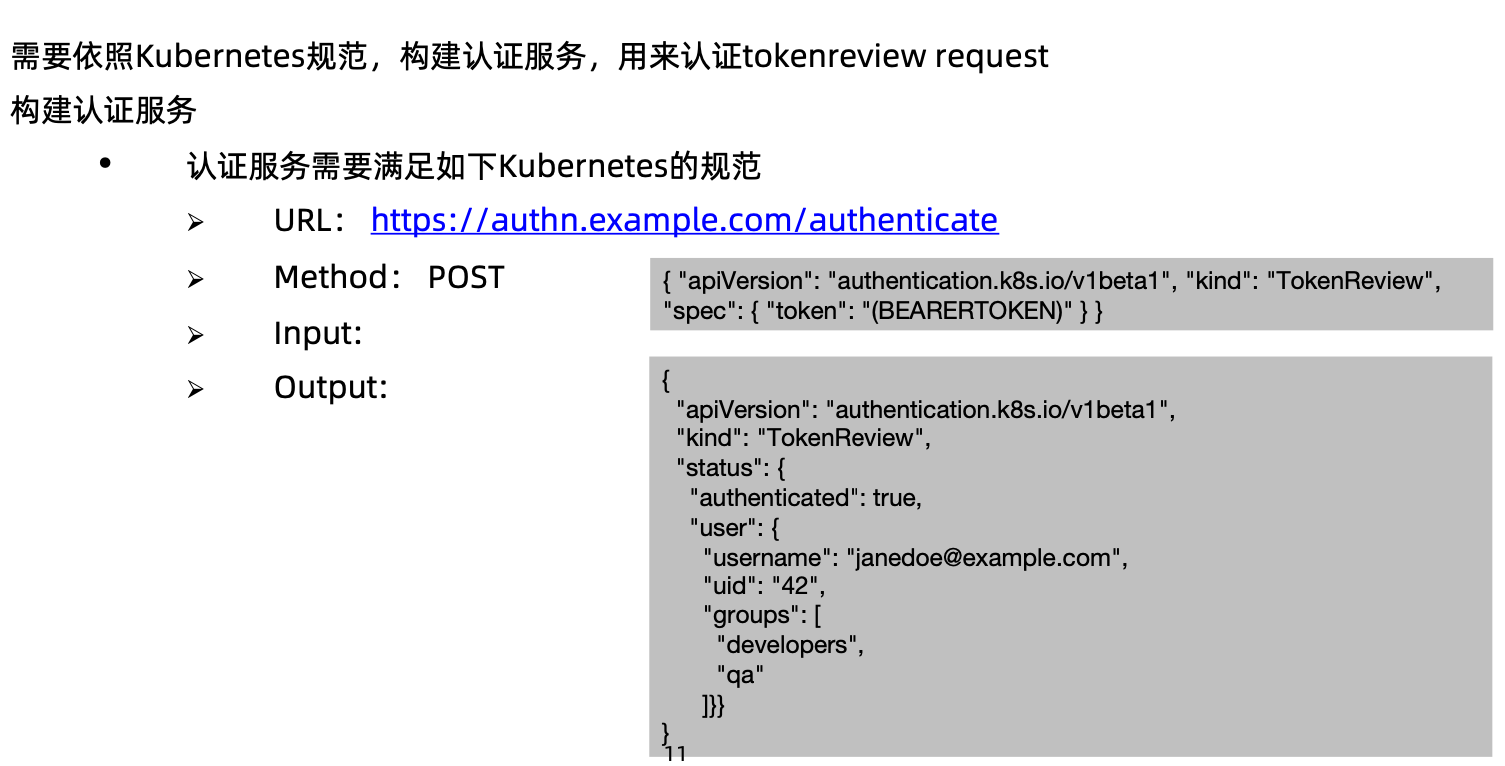
开发认证服务
package main |
配置认证服务和apiserver
最佳实践:webhook的认证和鉴权服务,通过sidercar的模式,跑在apiserver服务上

{ |
生产系统中遇到的陷阱

鉴权
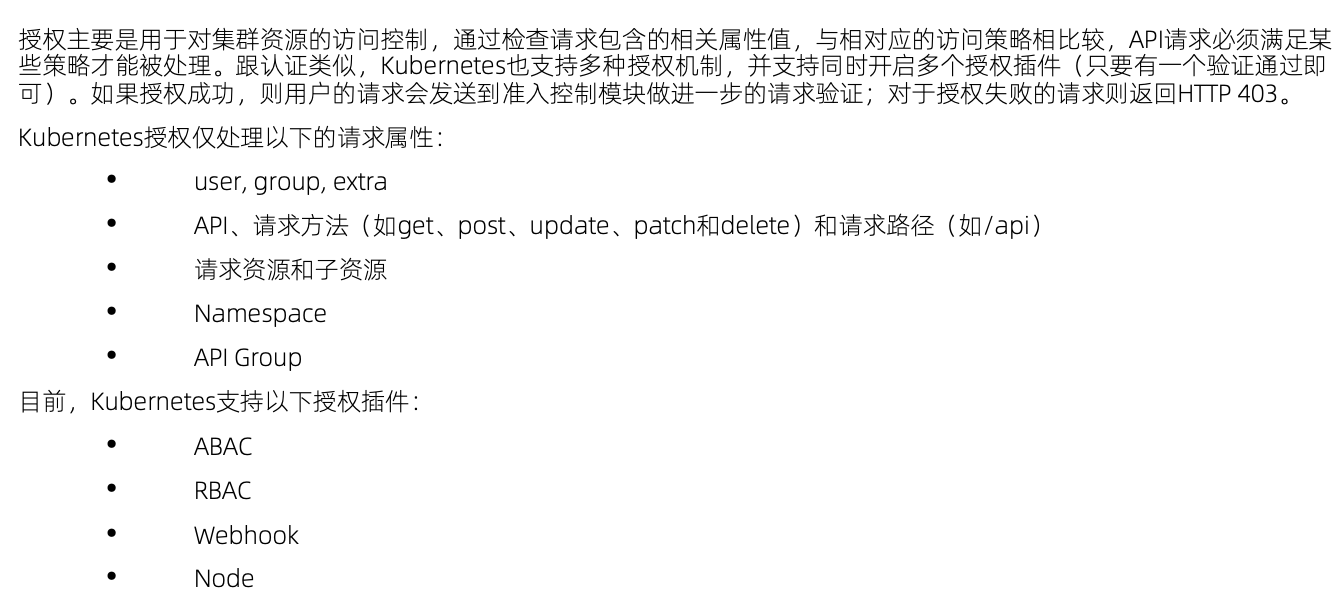
RBAC vs ABAC
RBAC图解
老版本
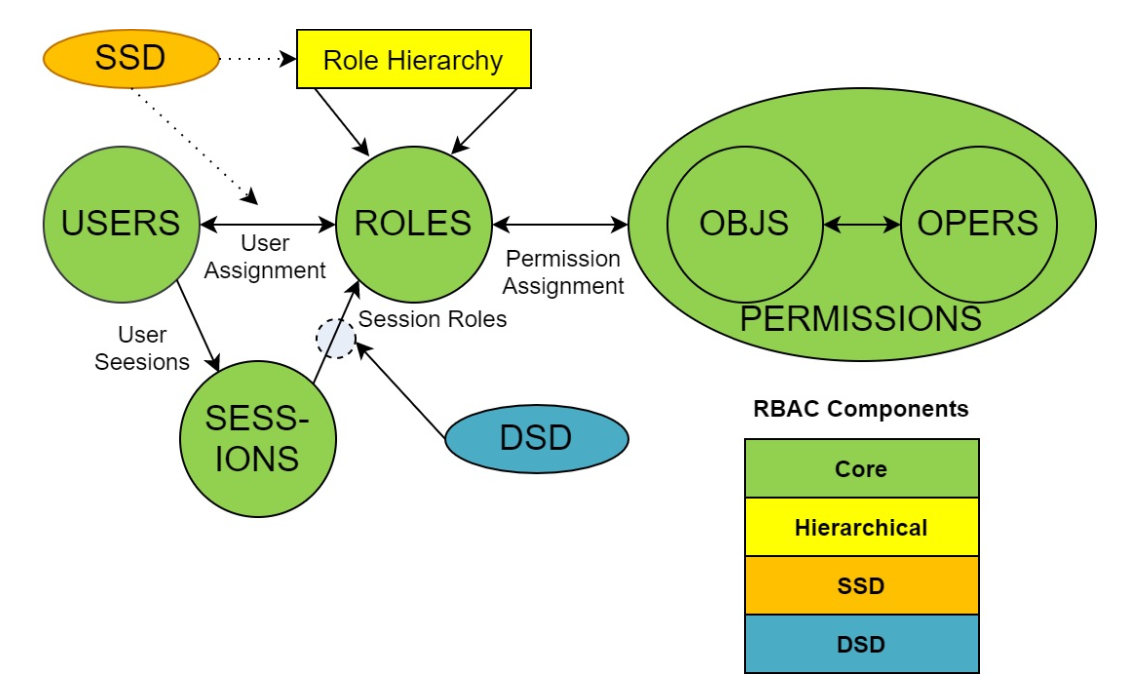
新版本
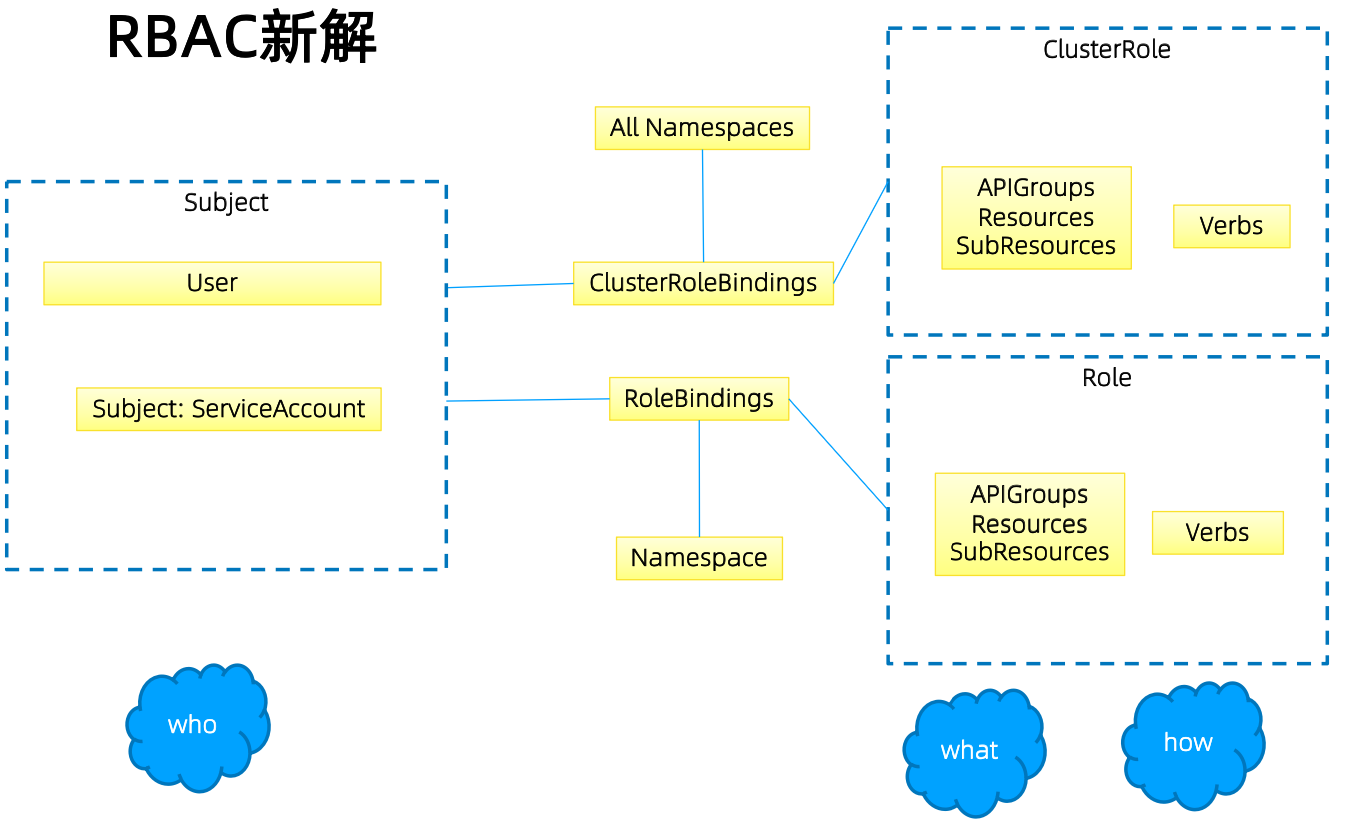
Role和ClusterRole

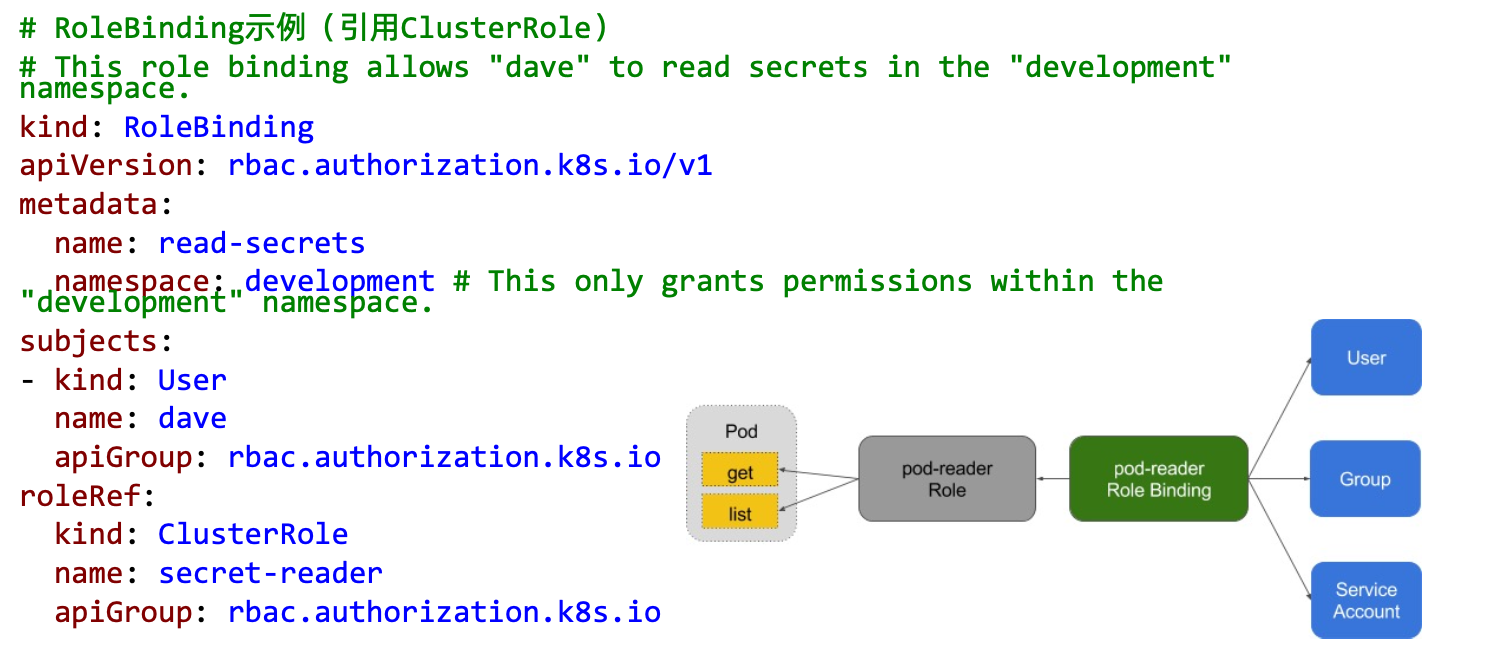
binding
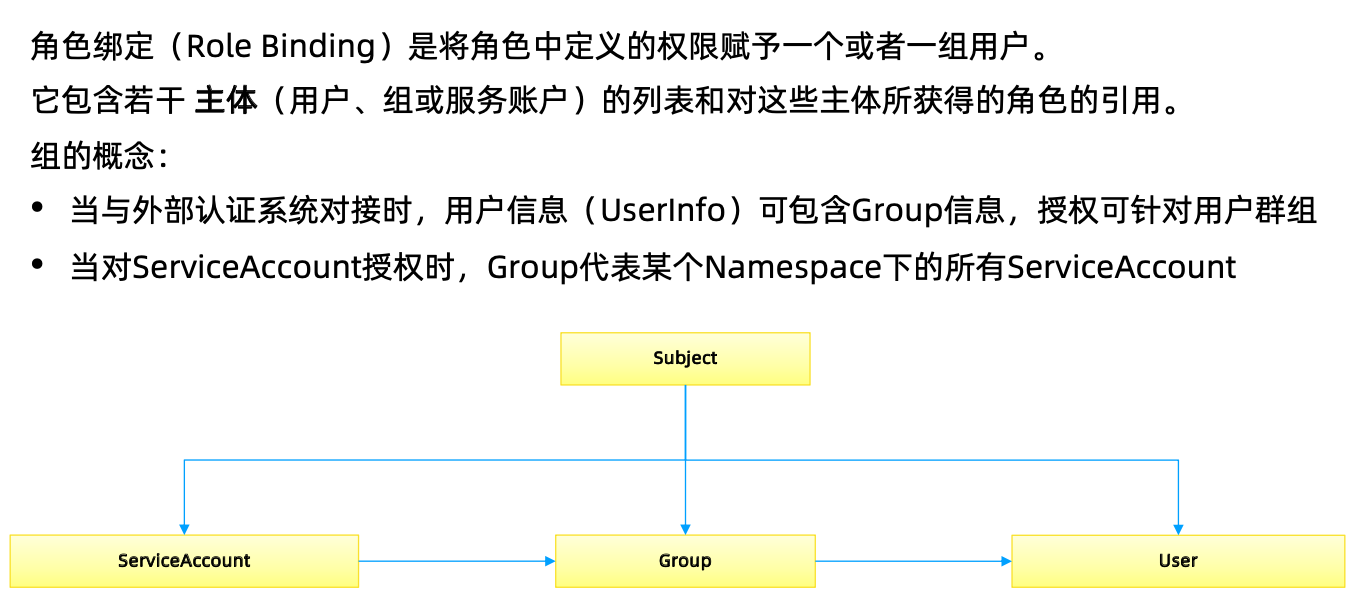
账户/组的管理
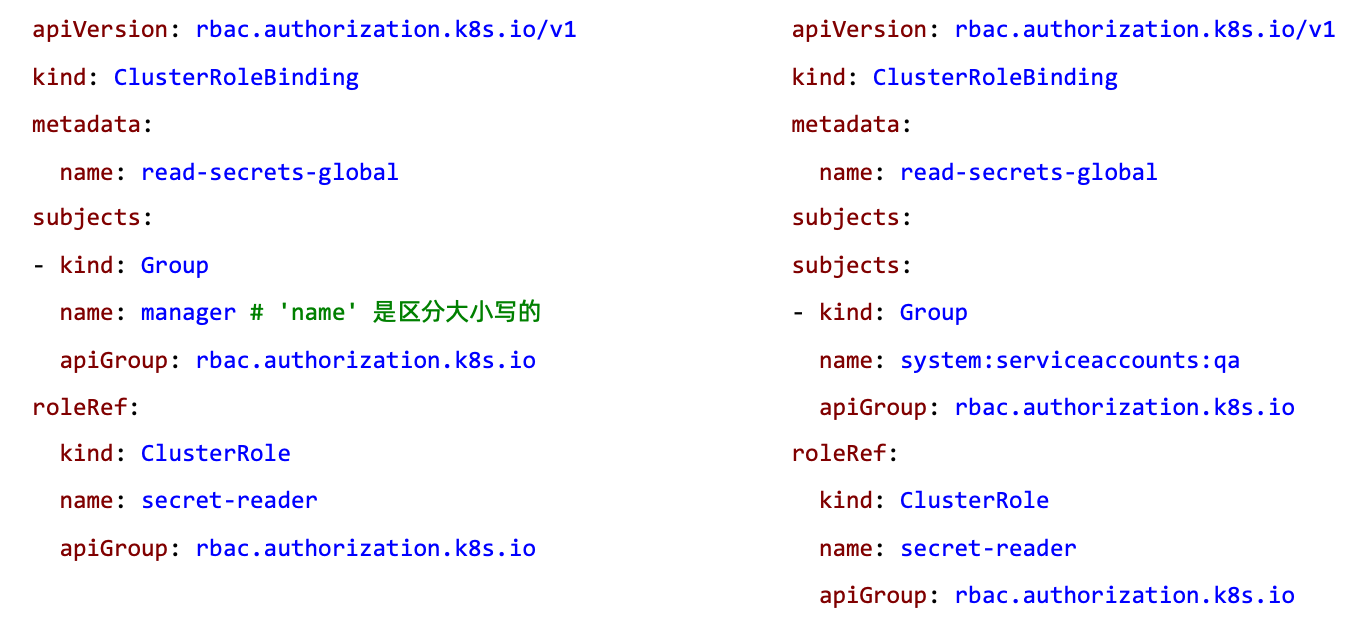
针对群组授权
规划系统角色
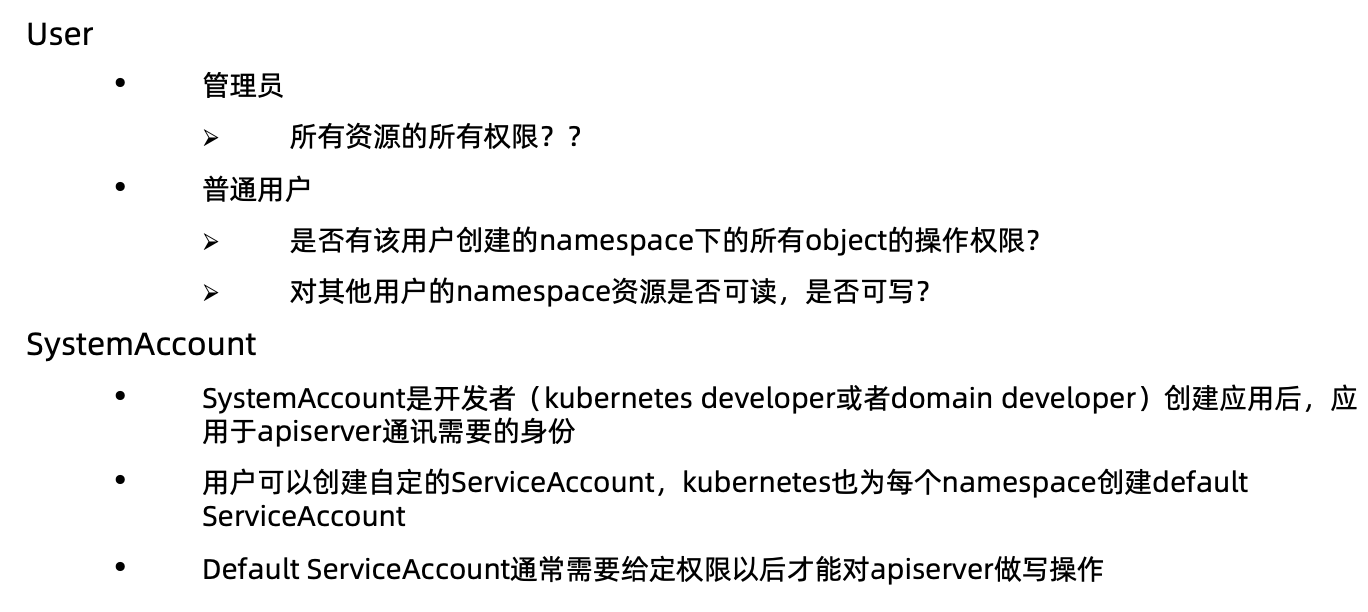
实现方案

与权限相关的其他最佳实践

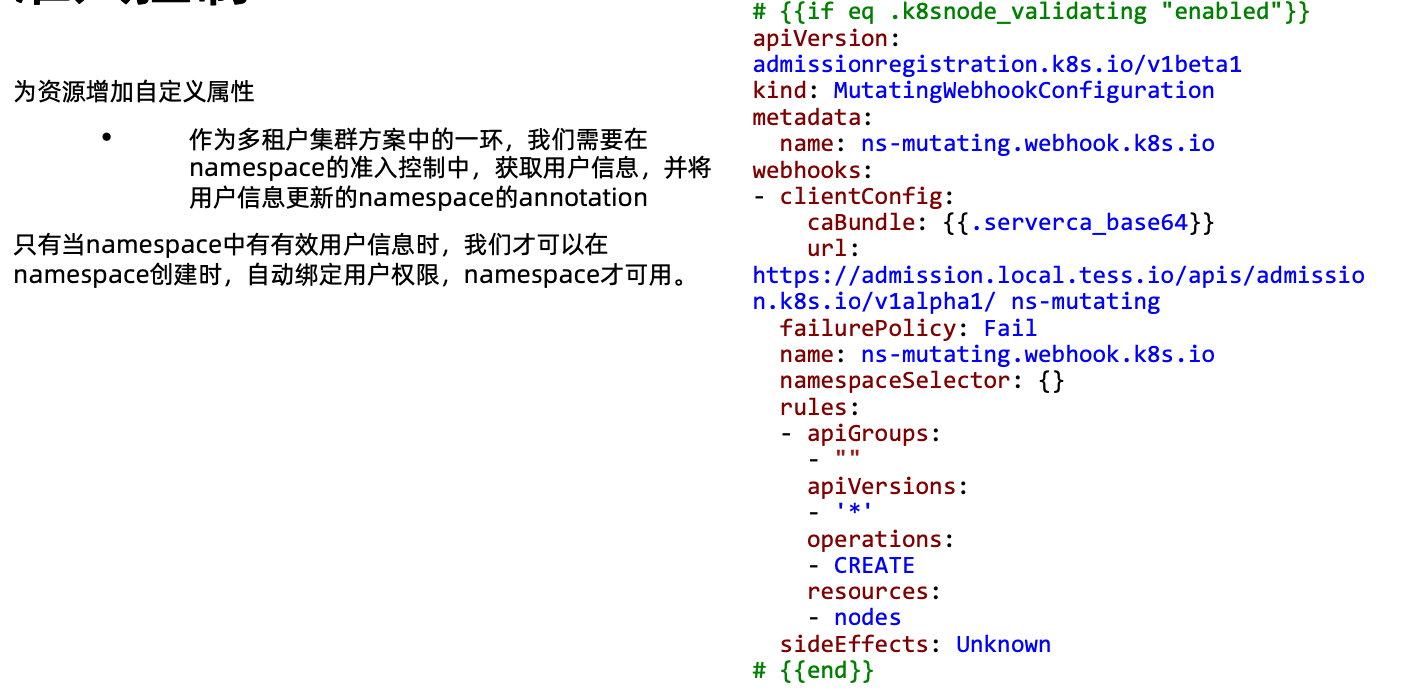
准入
准入控制


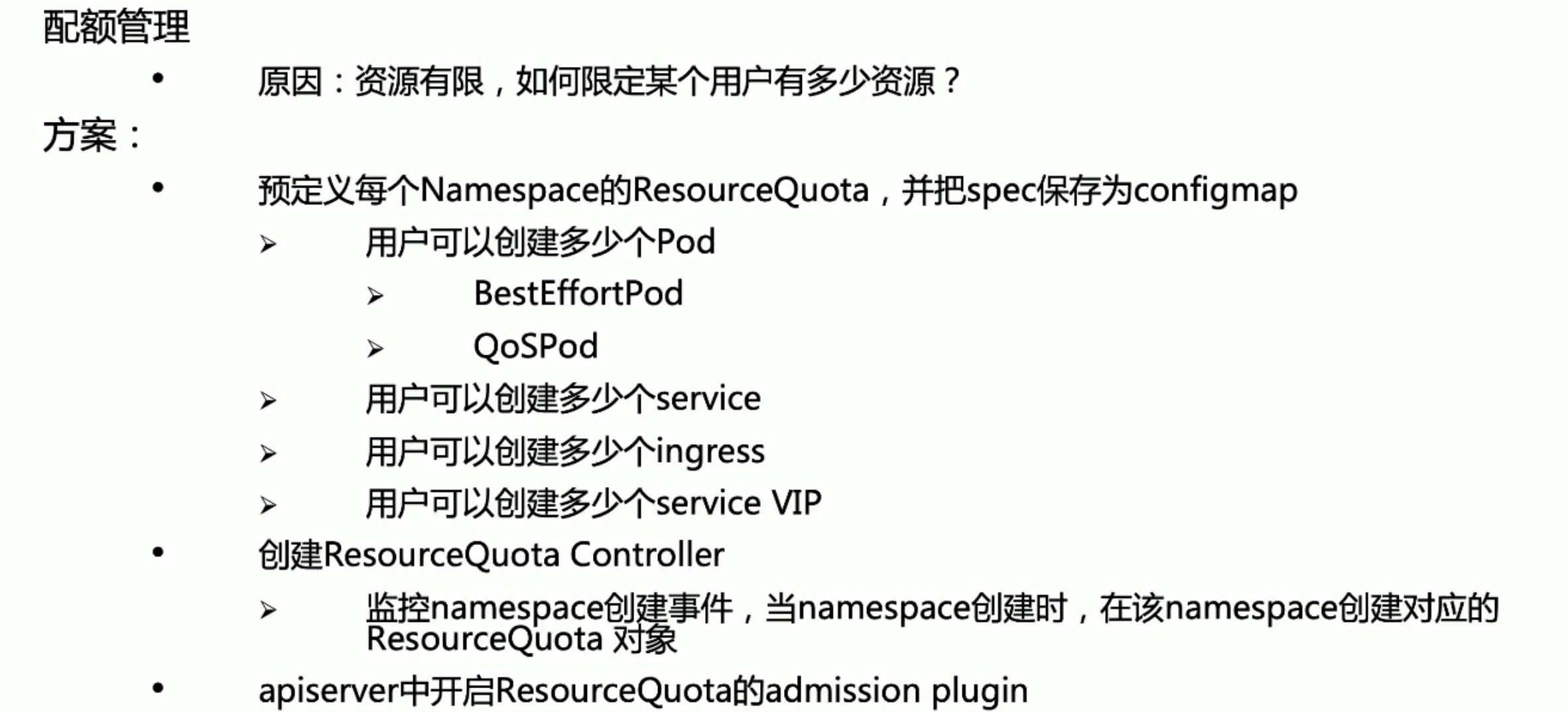
准入控制插件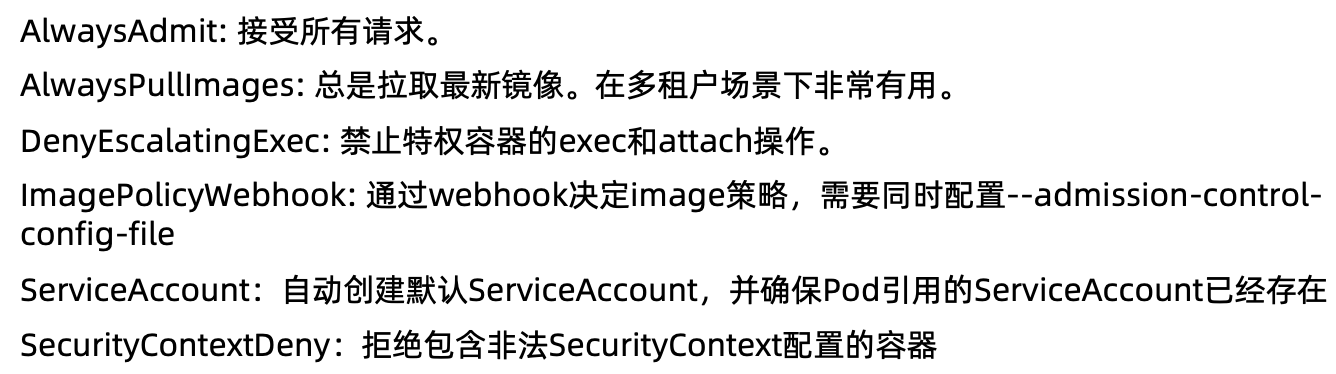

准入控制插件的开发
准入控制插件
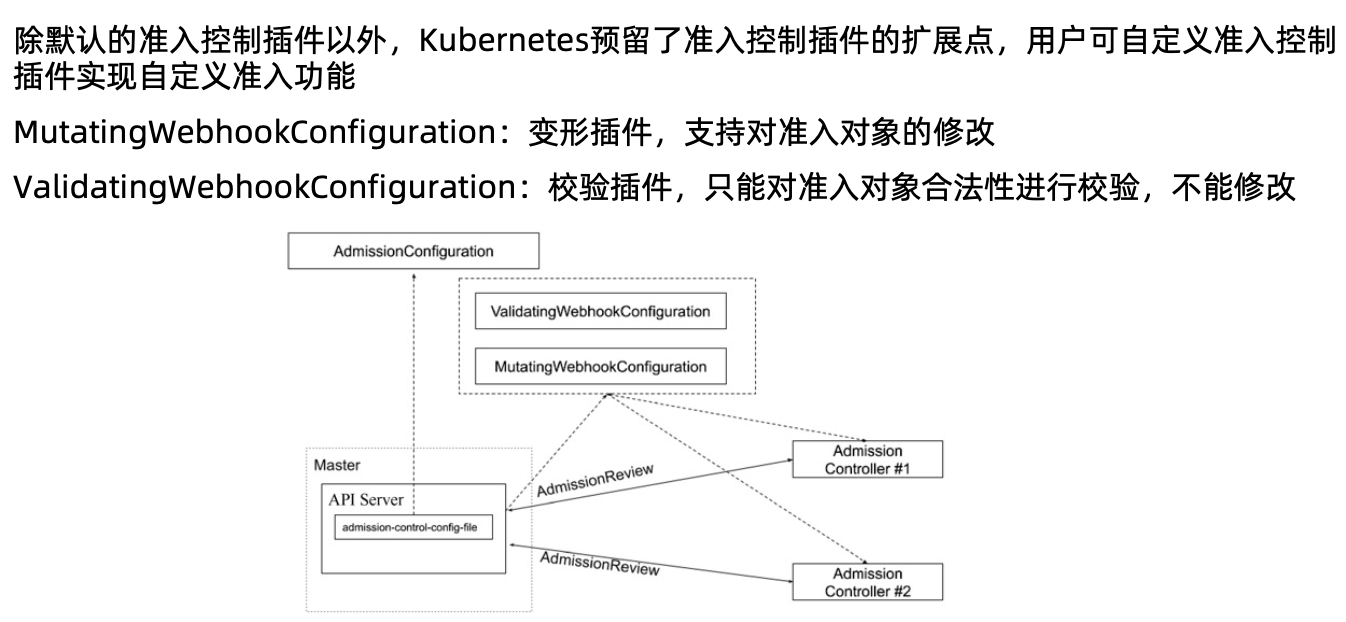
限流
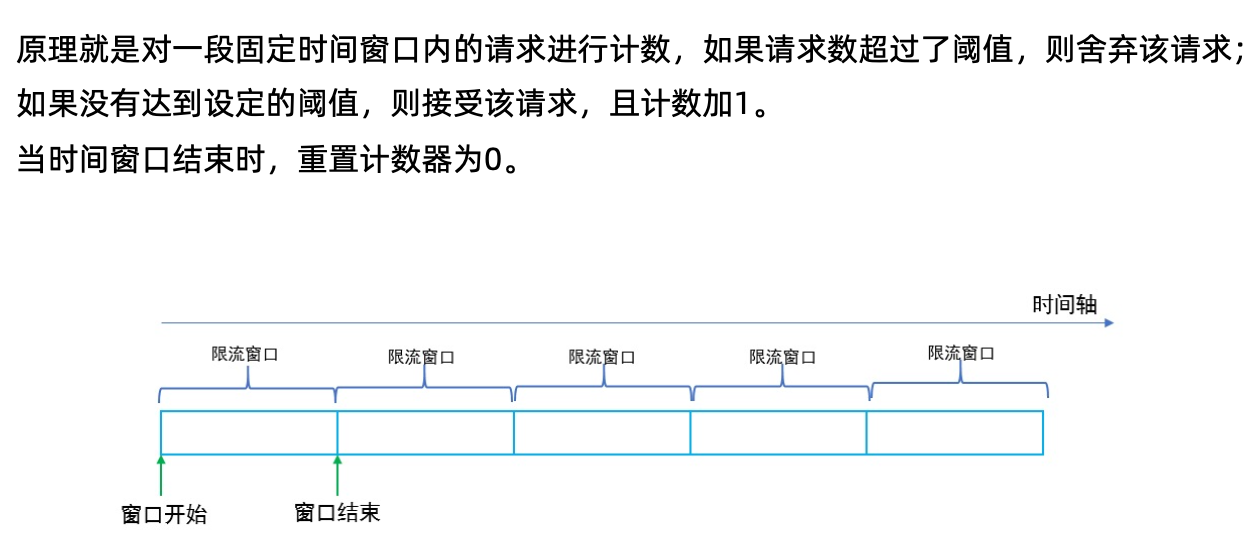
计数器固定窗口算法
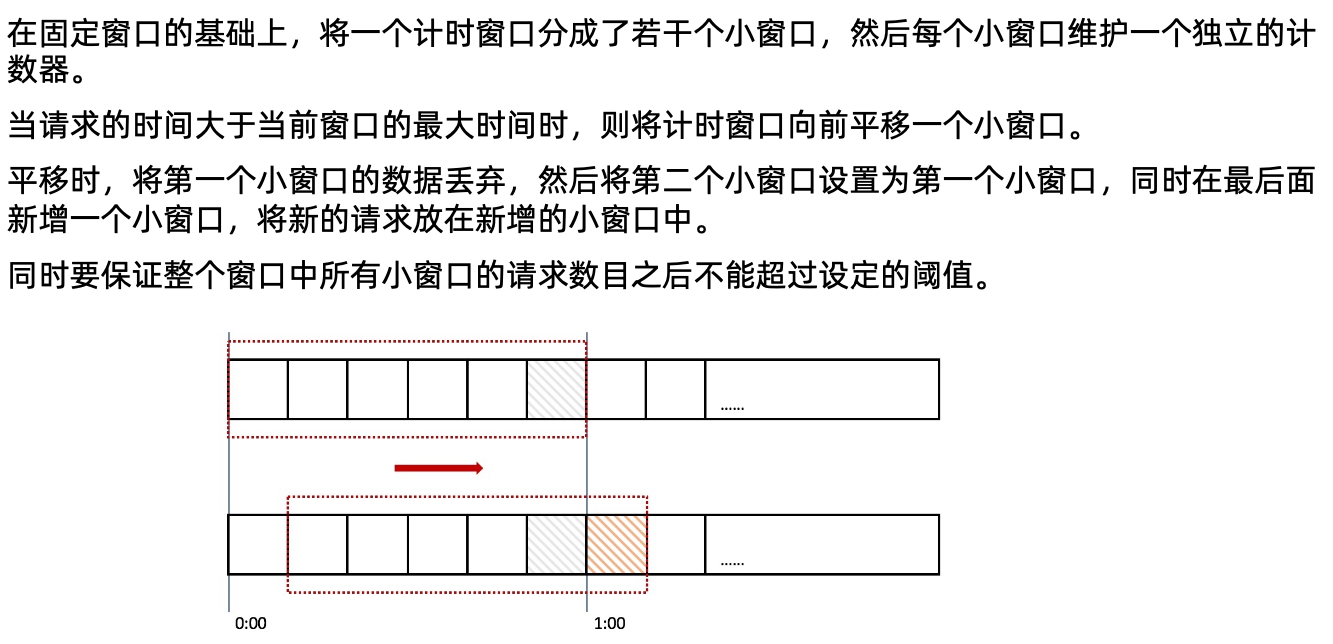
计数器滑动窗口算法
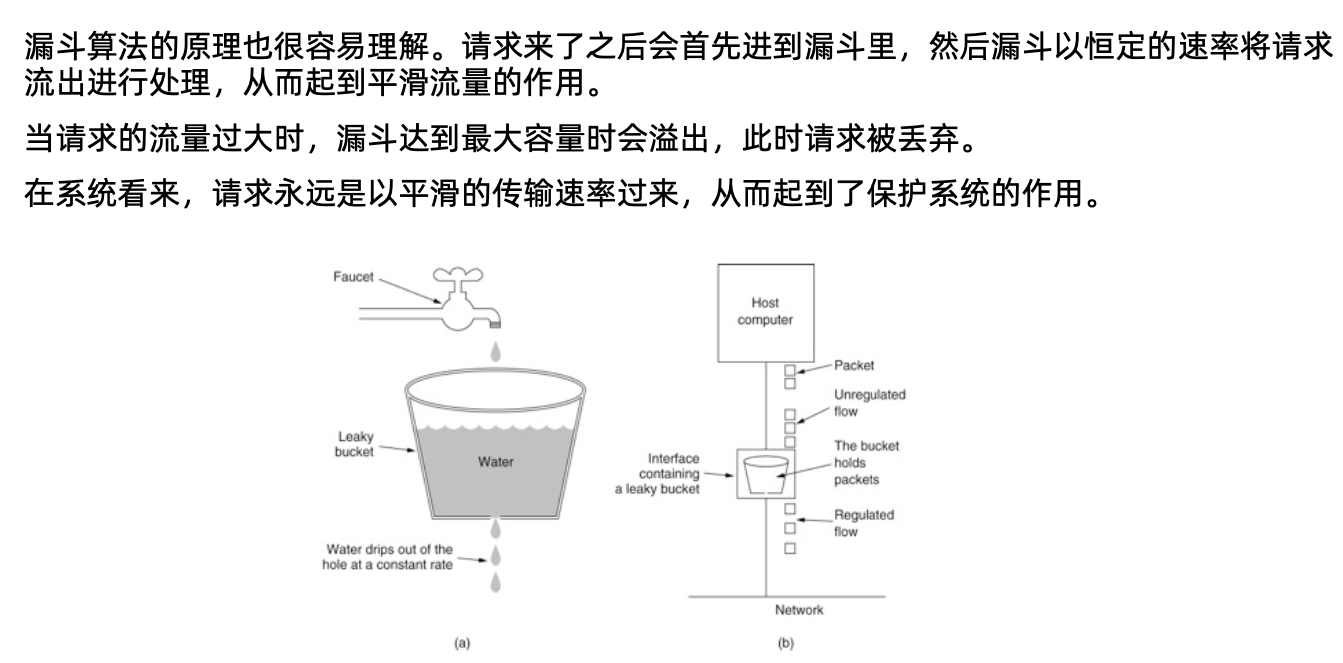
漏斗算法
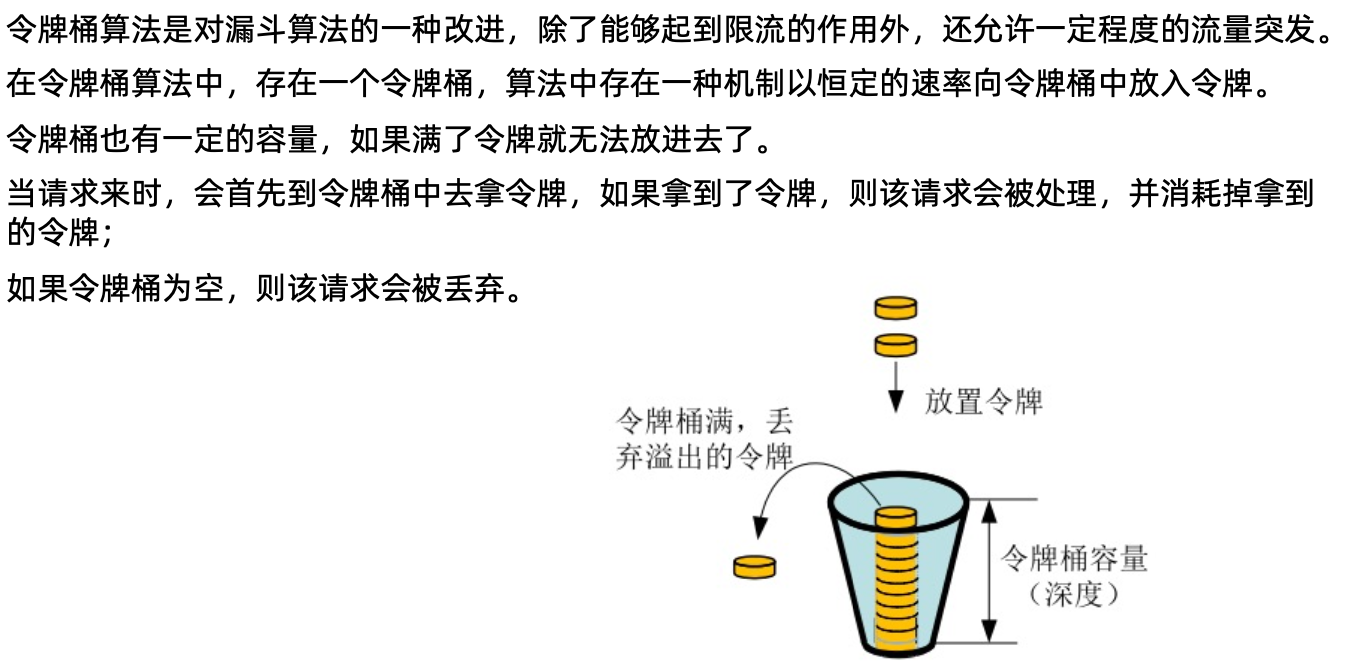
令牌桶算法
ApiServer中的限流
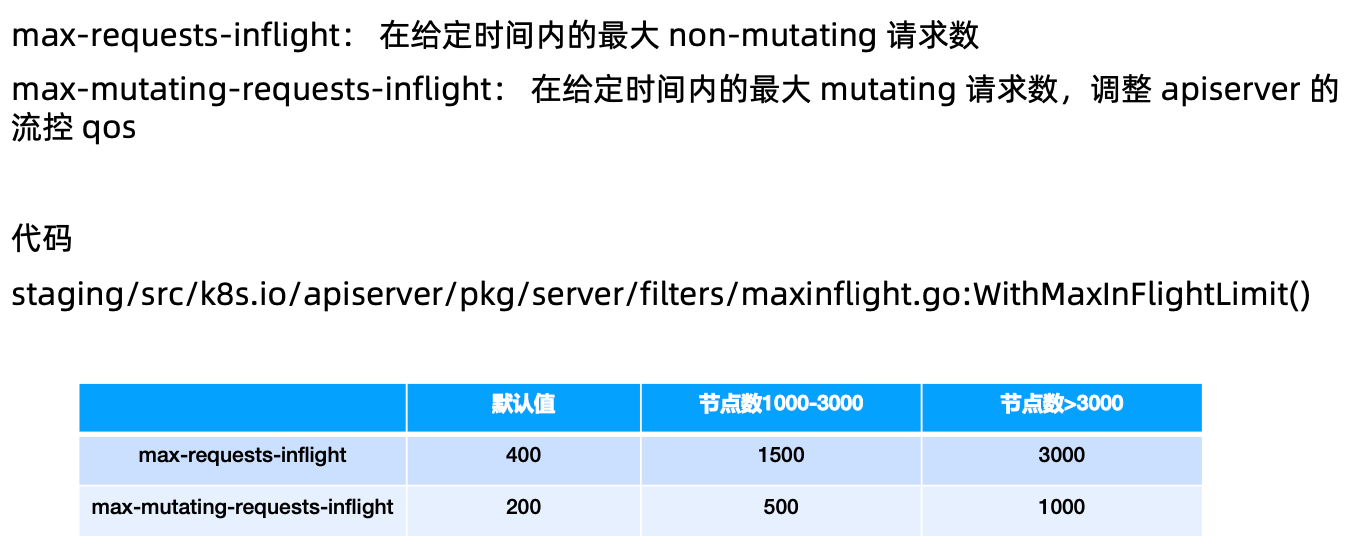
传统限流方法的局限性

API Priority and Fairness
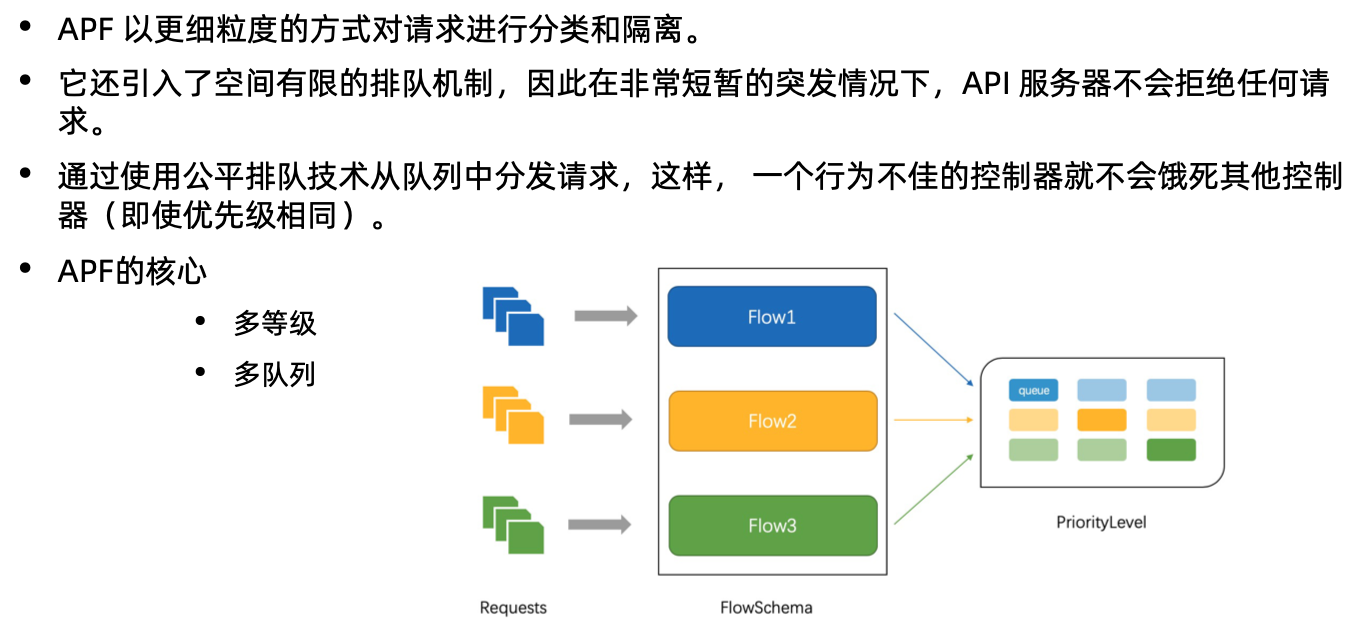

概念
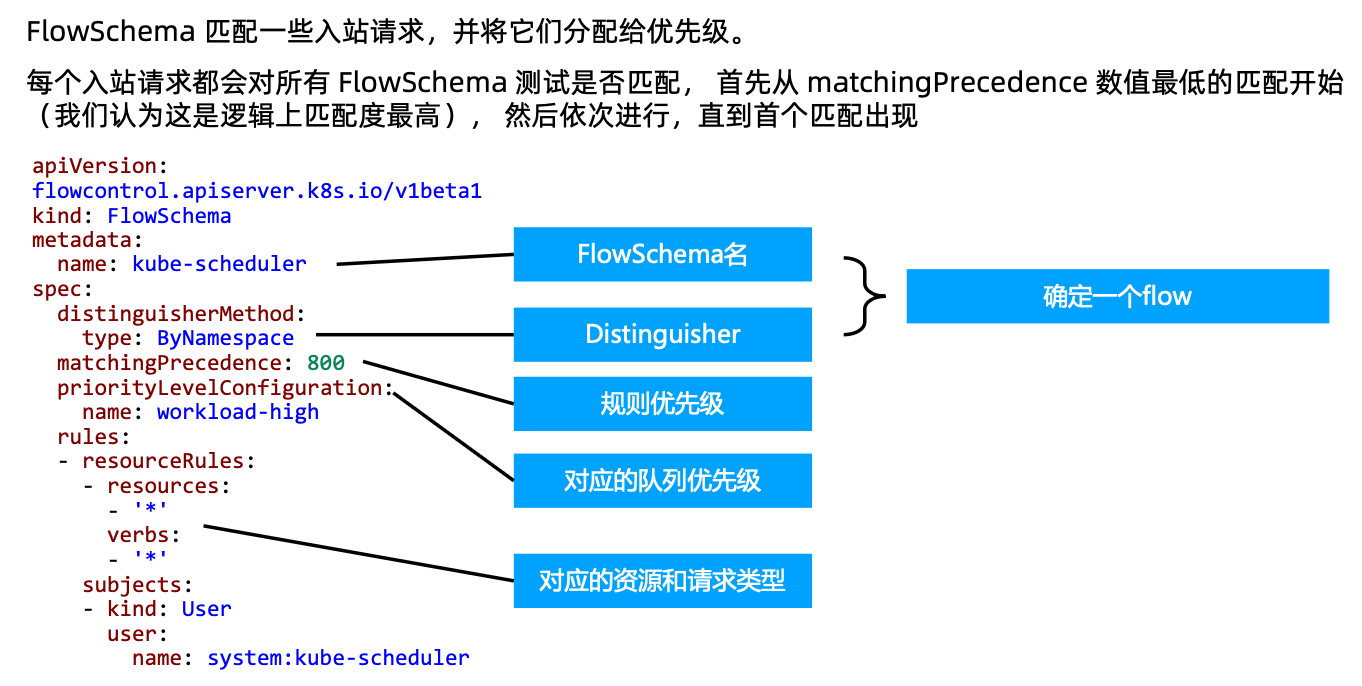
优先级

排队

豁免请求
某些特别重要的请求不受制于此特性施加的任何限制。这些豁免可防止不当的流控配置完全禁用 API 服务器。
默认配置


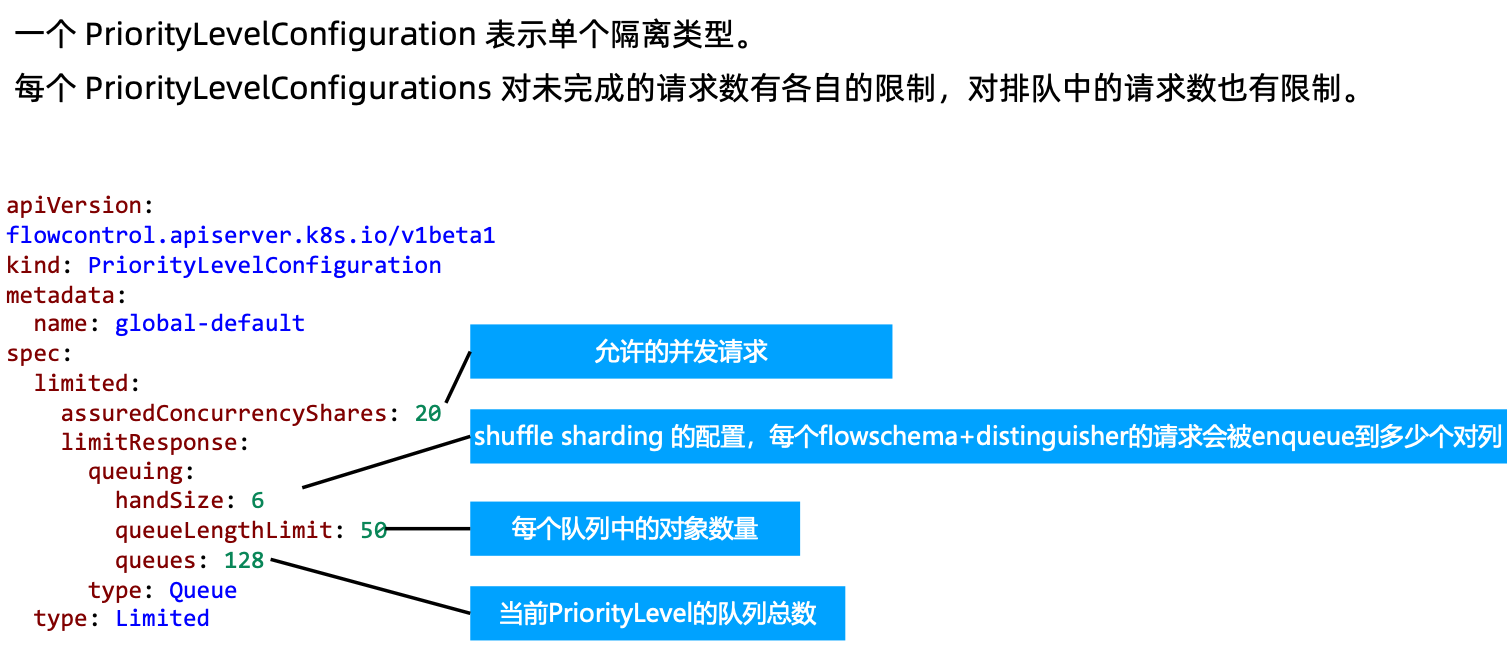
PriorityLevelConfiguration
FlowSchema
调试

高可用ApiServer
启动ApiServer示例
kube-apiserver |
构建高可用的多副本apiServer
最佳实践还是采用静态pod的方式来部署多副本apiserver,依托于k8s给我们提供了可靠的服务,还可以使用k8s的探活策略等。而不是采用二进制的systemctld。

预留充足的CPU、内存资源

善用速率限制(RateLimit)

设置合适的缓存大小

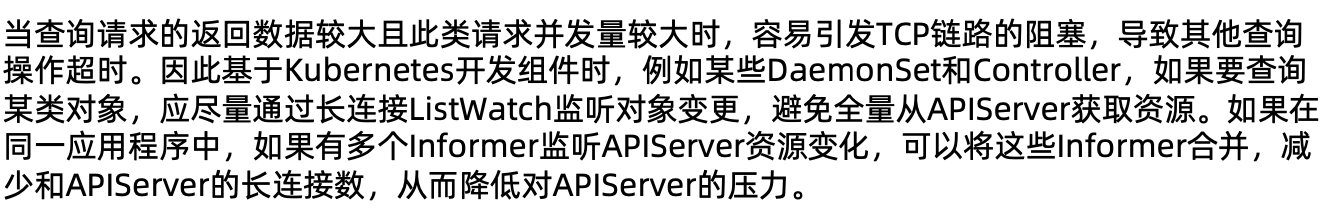
客户端尽量使用长连接
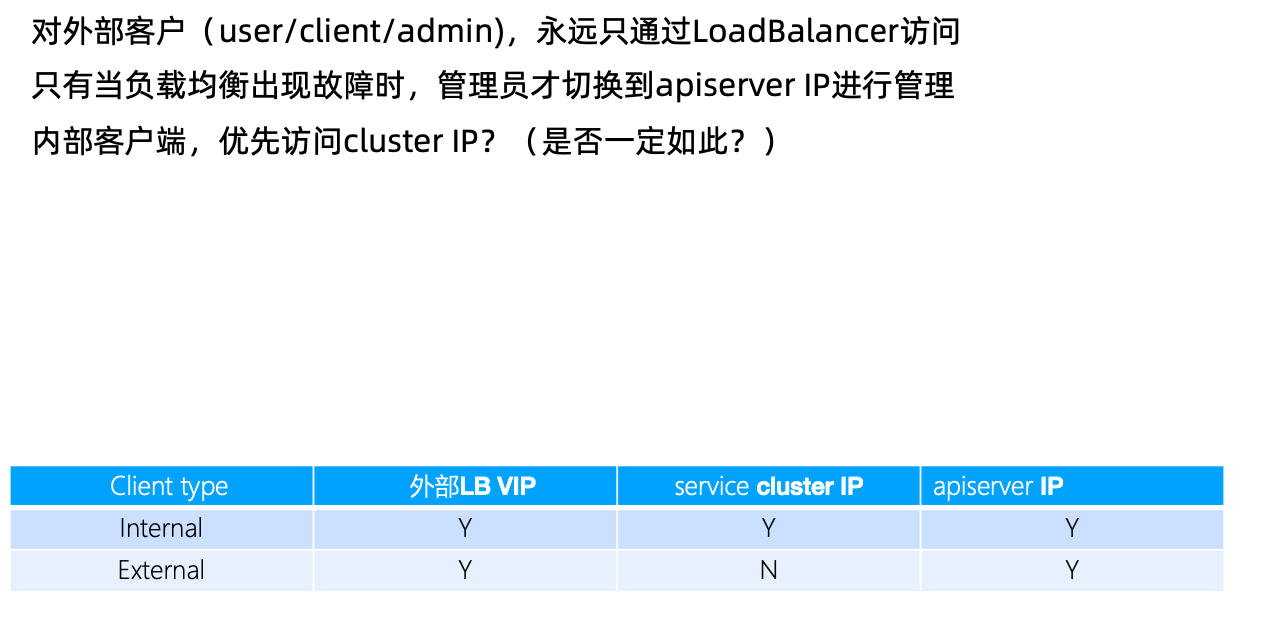
如何访问APIServer
搭建多租户的Kubernetes集群

认证
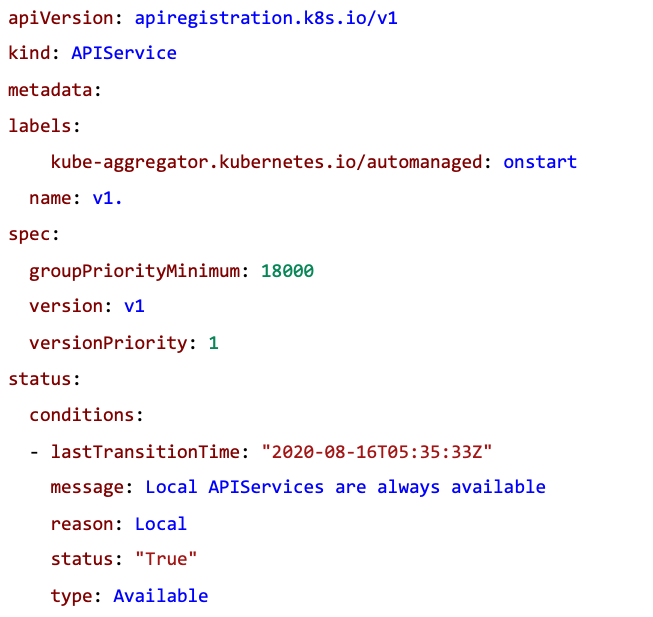
注册apiserver
授权
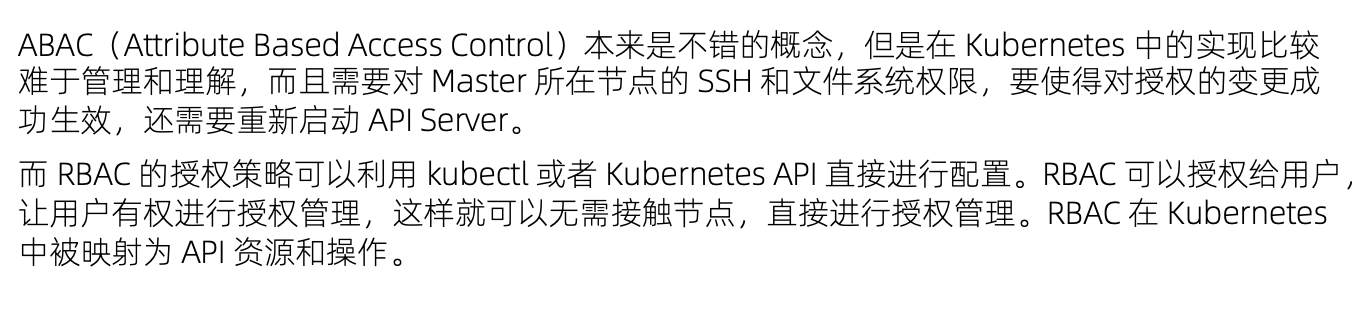
ABAC有期局限性,针对每个account都需要做配置,并且需要重启apiserver RBAC更灵活,更符合我们通常熟知的权限管理
RBAC
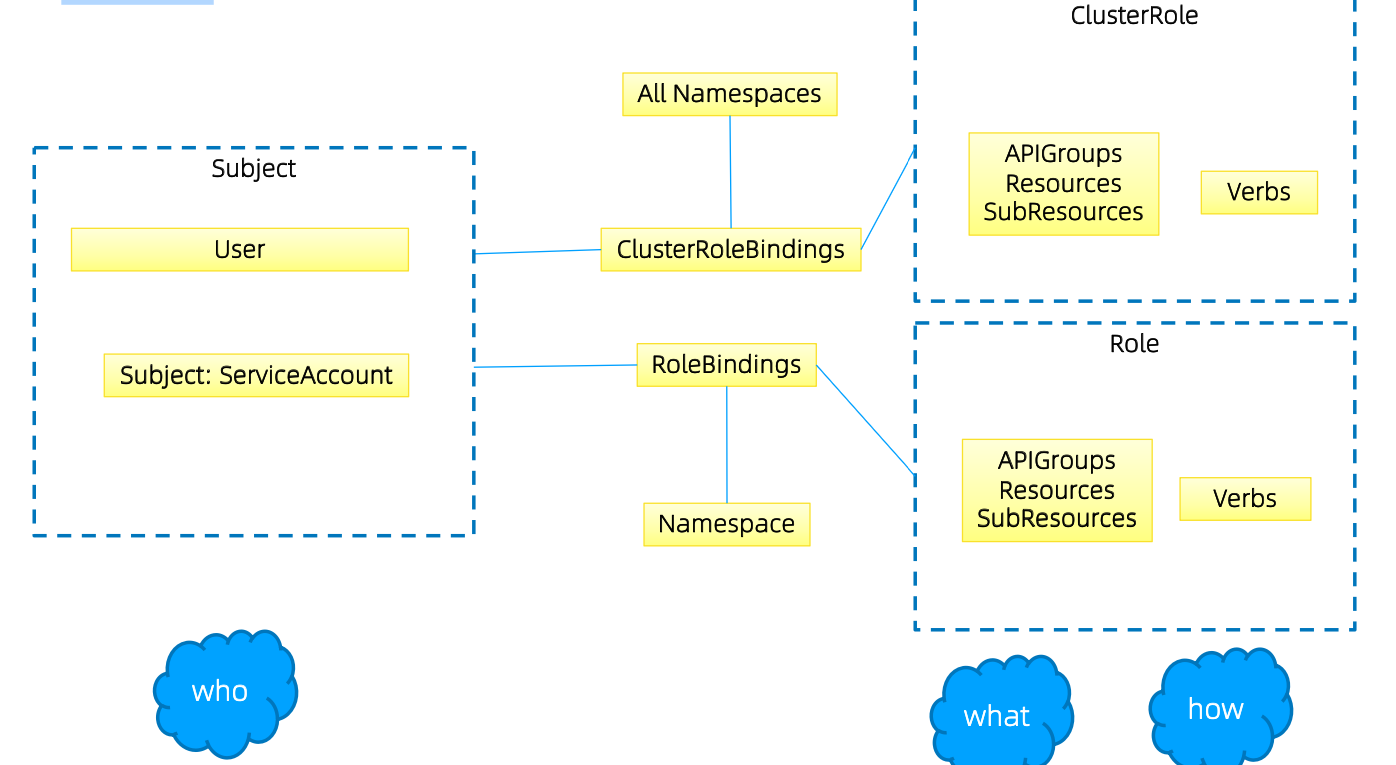
规划系统角色
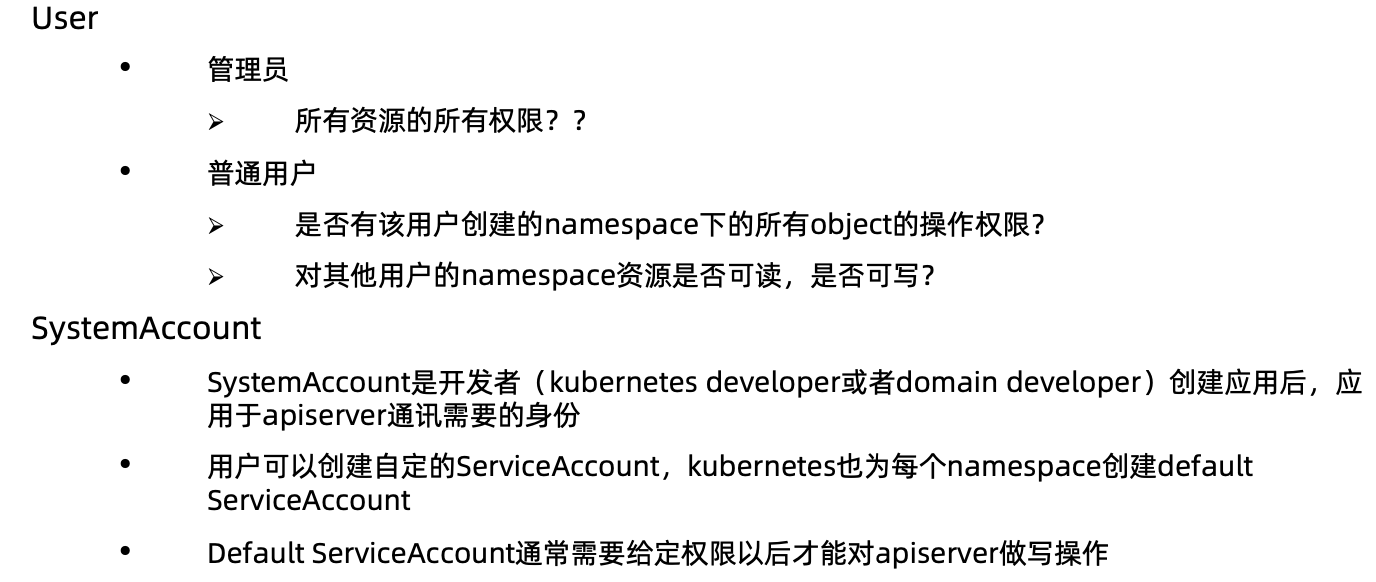
实现方案

与权限相关的其他最佳实践

apimachinery
回顾GKV

如何定义Group
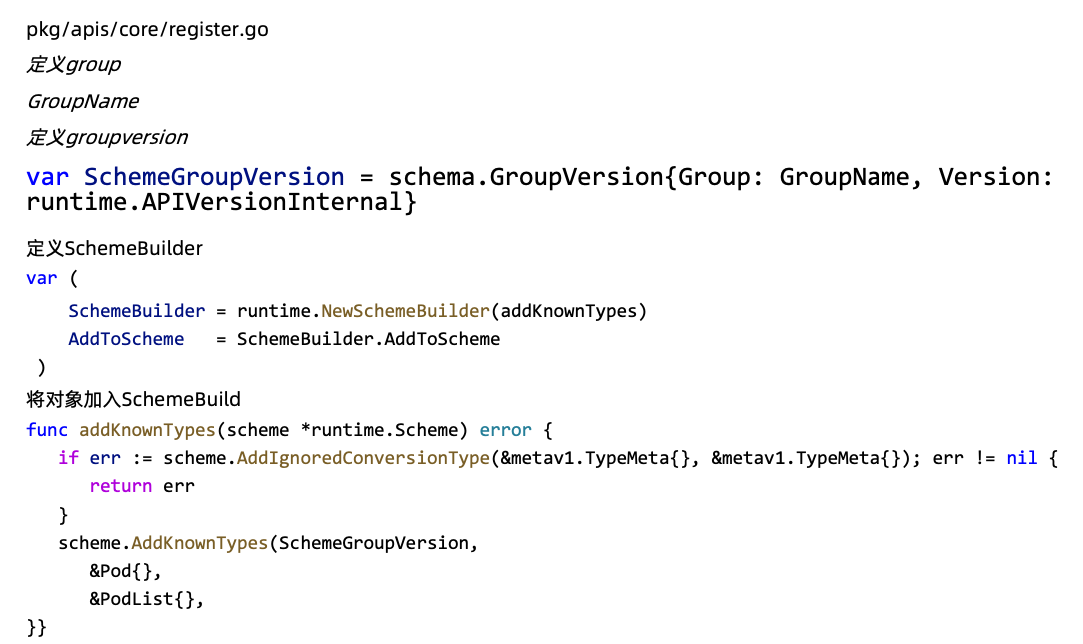
定义对象类型 types.go
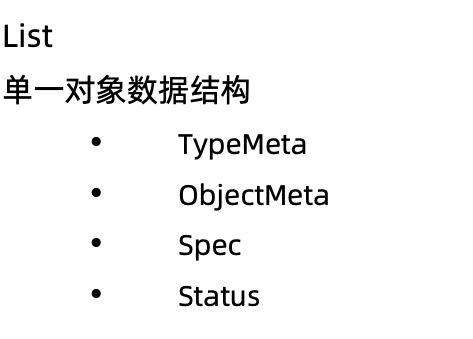
代码生成Tags
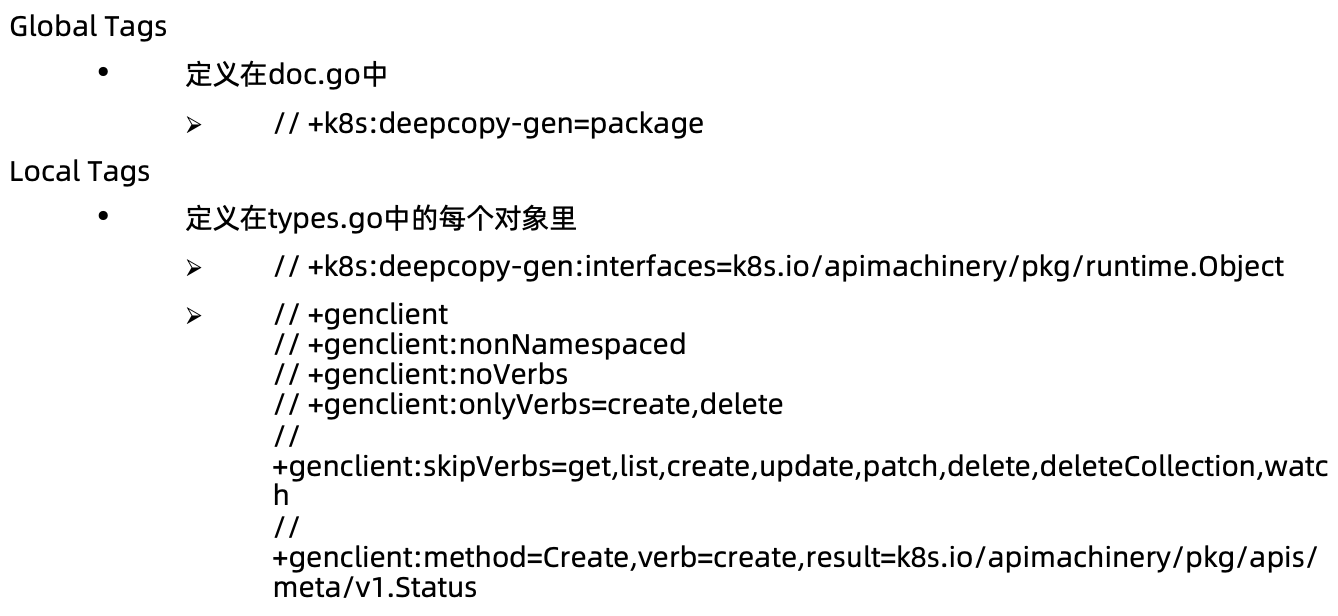
实现etcd storage
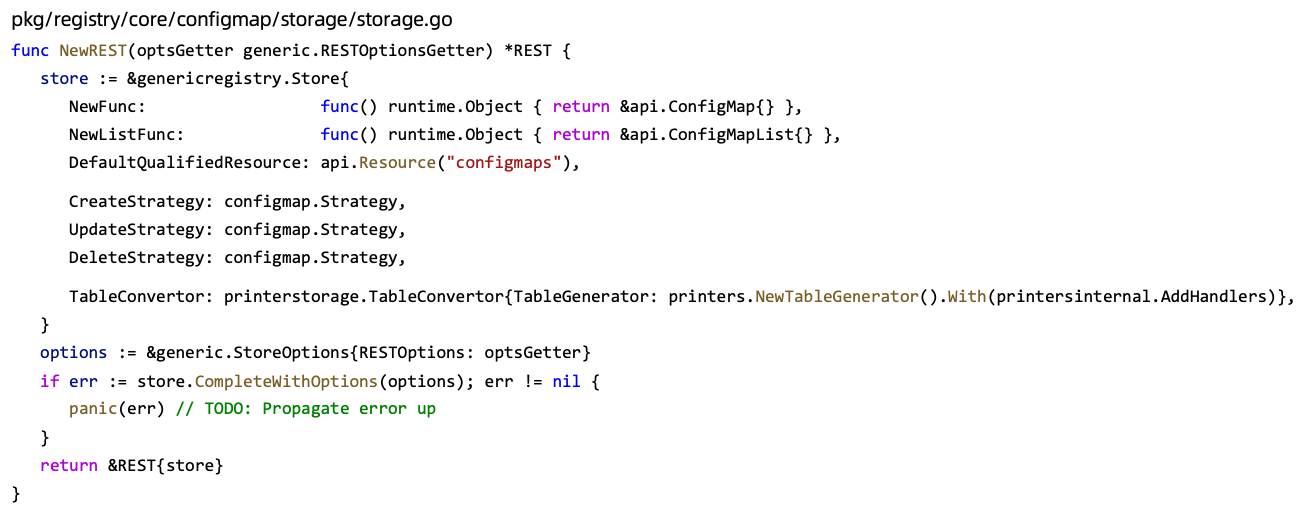
代码生成
https://github.com/kubernetes/code-generator |
